Swift-based ransomware attacks macOS pirates through false decryption promise
A new ransomware created in Swift encrypting the user’s files and demanding a payment has appeared , targeting macOS users who don’t want to pay for legitimate software, according to AppleInsider’s report. It’s disguised as common apps like Adobe CC or Office for Mac 2016 and spreads. Once infected, the computer’s file and data will be encrypted, and the user will be required for payment before unlocking them. In worse cases, even if you’ve paid as required, your files remain unavailable.

Marc-Etienne M.Léveillé, one of the security researchers, discovered that the ransomware was firstly circulated via BitTorrent sites and called “Patcher.” It poses as a crack for pirates to get around copy protection and licensing systems used in popular software suites.
Currently it has been found to be posing as ways to unlock Microsoft Office for Mac 2016 and Adobe Premiere Pro CC 2017. When extracted from the archive and executed, the ransomware opens up a window advising users to press the start button to patch the pirated software. If clicked, it will spread around a “Read me” file to various user directories, before encrypting all other user files using a randomly-generated 25-character key in an archive, and deleting the original files.
The researcher notes the ransomware is “generally poorly coded” in various ways. Produced using Swift, the application’s window is impossible to open if it is closed, while code to try and use Disk Utility to null the free space on the root partition uses the wrong path to the tool.
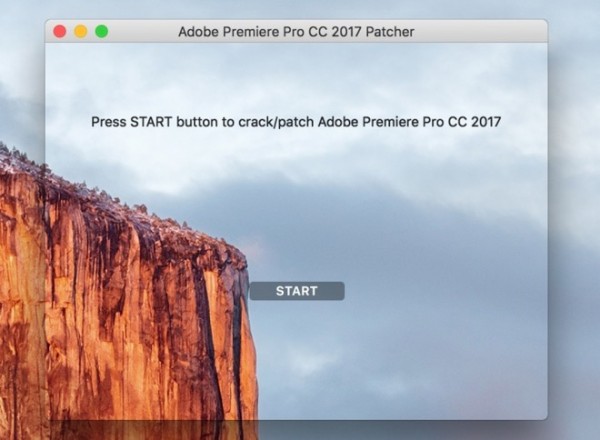
There is no code in the malware that sends the key to the operator, so there is no possibility of providing the “service” of decrypting the files for the user, while the length of the key also suggests a brute force attack would take too long to accomplish.
Researcher Léveillé suggests having a current offline backup of all important data, as well as security software, to help protect against similar threats.
